Reports
The Global Hardware Encryption Market is projected to expand at a substantial CAGR of 10.7% from 2023 to 2030, fueled by factors such as the growing volume of sensitive data, rising cybersecurity concerns, and increasing demand for data privacy and compliance solutions. Hardware encryption refers to the process of encrypting and decrypting data using dedicated cryptographic hardware devices integrated into computer systems, storage devices, and communication networks. These hardware-based encryption solutions offer robust security measures to protect sensitive data from unauthorized access, data breaches, and cyber threats. The Hardware Encryption Market is witnessing significant growth driven by the increasing adoption of data encryption solutions across various industries to safeguard confidential information, comply with data protection regulations, and mitigate security risks. Hardware encryption solutions leverage advanced encryption algorithms such as Advanced Encryption Standard (AES), Rivest-Shamir-Adleman (RSA), and Elliptic Curve Cryptography (ECC) to ensure data confidentiality, integrity, and authenticity.
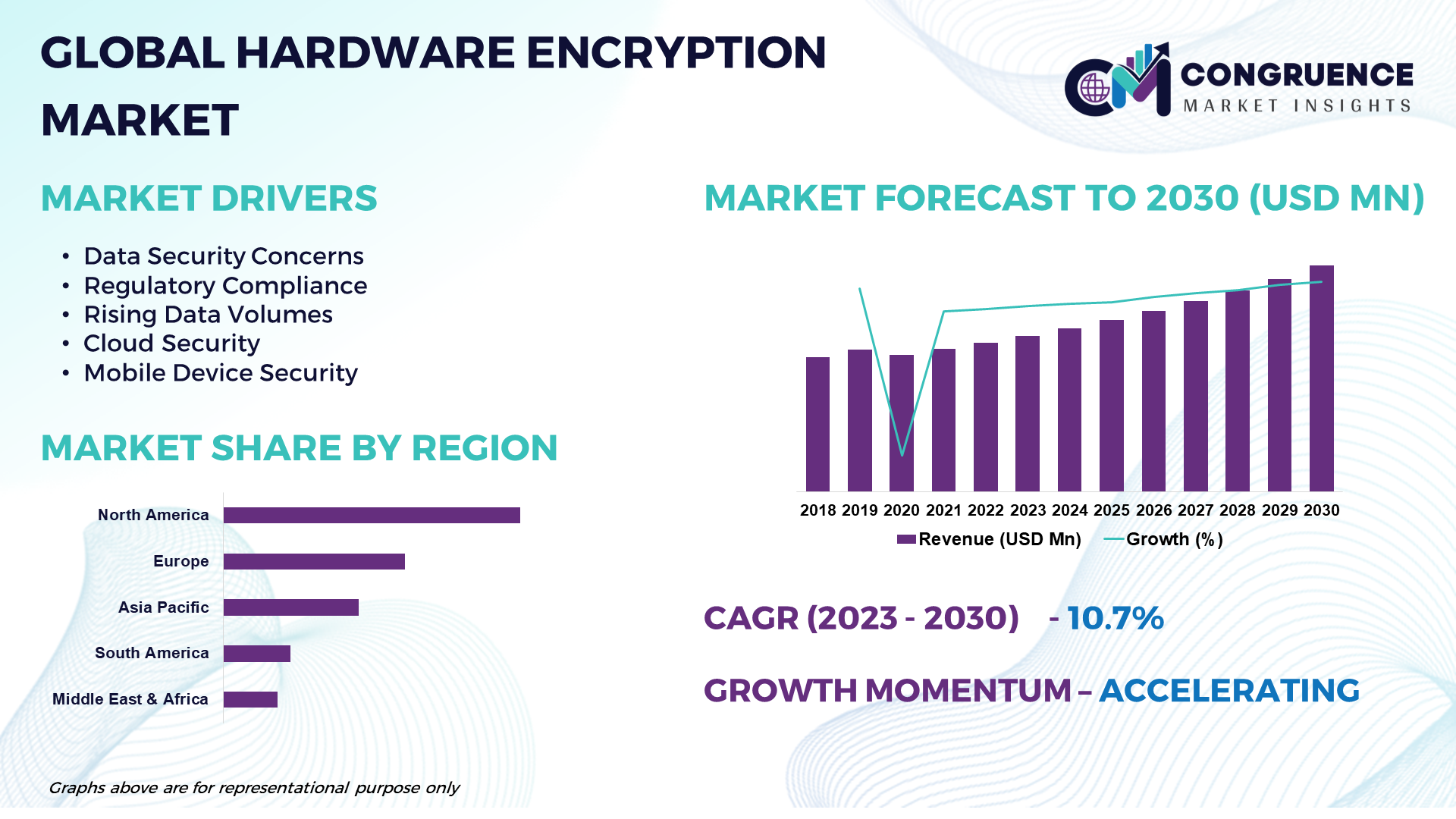
Hardware Encryption Market Major Driving Forces
Data Security Concerns: The escalating cybersecurity threats, data breaches, and privacy breaches are driving organizations across industries to adopt hardware encryption solutions to protect sensitive data and ensure regulatory compliance with data protection laws such as GDPR, HIPAA, and PCI DSS.
Regulatory Compliance: The stringent data protection regulations and compliance requirements imposed by government authorities and industry standards bodies are driving the adoption of hardware encryption solutions to secure sensitive data, safeguard customer privacy, and avoid costly fines and penalties for non-compliance.
Rising Data Volumes: The exponential growth of digital data generated by organizations, individuals, and connected devices is driving the demand for hardware encryption solutions to encrypt data-at-rest and data-in-transit, ensuring confidentiality, integrity, and availability of information assets.
Cloud Security: The increasing adoption of cloud computing services and hybrid cloud environments is driving the demand for hardware encryption solutions to protect data stored, processed, and transmitted in cloud-based applications and services, ensuring data sovereignty, confidentiality, and compliance with cloud security standards.
Mobile Device Security: The proliferation of mobile devices such as smartphones, tablets, and laptops in enterprise environments is driving the adoption of hardware encryption solutions to secure data stored on mobile devices, prevent unauthorized access, and protect against mobile threats such as theft, loss, and malware attacks.
Hardware Encryption Market Key Opportunities
IoT Security: The growing adoption of Internet of Things (IoT) devices and connected sensors in smart homes, smart cities, industrial automation, and healthcare applications presents opportunities for hardware encryption vendors to develop specialized solutions for securing IoT data, communications, and devices.
Blockchain Security: The increasing adoption of blockchain technology in various industries such as finance, supply chain, healthcare, and government presents opportunities for hardware encryption vendors to provide secure hardware wallets, key management solutions, and hardware security modules (HSMs) for blockchain-based applications and digital assets.
Quantum Computing Resistance: The emergence of quantum computing technologies poses a threat to conventional encryption algorithms such as RSA and ECC, creating opportunities for hardware encryption vendors to develop quantum-resistant encryption solutions based on post-quantum cryptography (PQC) algorithms and hardware security architectures.
Endpoint Security: The rising demand for endpoint security solutions to protect against malware, ransomware, and insider threats presents opportunities for hardware encryption vendors to integrate encryption capabilities into endpoint security platforms, ensuring data protection and compliance on desktops, laptops, and mobile devices.
Data Center Security: The increasing adoption of hardware encryption solutions in data center environments to secure data storage systems, network communications, and virtualized workloads presents opportunities for hardware encryption vendors to provide scalable, high-performance encryption solutions for data center infrastructure and cloud services.
Hardware Encryption Market Key Trends
· Data Security Concerns: The escalating cybersecurity threats, data breaches, and privacy breaches are driving organizations across industries to adopt hardware encryption solutions to protect sensitive data and ensure regulatory compliance with data protection laws such as GDPR, HIPAA, and PCI DSS.
· Regulatory Compliance: The stringent data protection regulations and compliance requirements imposed by government authorities and industry standards bodies are driving the adoption of hardware encryption solutions to secure sensitive data, safeguard customer privacy, and avoid costly fines and penalties for non-compliance.
· Rising Data Volumes: The exponential growth of digital data generated by organizations, individuals, and connected devices is driving the demand for hardware encryption solutions to encrypt data-at-rest and data-in-transit, ensuring confidentiality, integrity, and availability of information assets.
· Cloud Security: The increasing adoption of cloud computing services and hybrid cloud environments is driving the demand for hardware encryption solutions to protect data stored, processed, and transmitted in cloud-based applications and services, ensuring data sovereignty, confidentiality, and compliance with cloud security standards.
· Mobile Device Security: The proliferation of mobile devices such as smartphones, tablets, and laptops in enterprise environments is driving the adoption of hardware encryption solutions to secure data stored on mobile devices, prevent unauthorized access, and protect against mobile threats such as theft, loss, and malware attacks.
Market Competition Landscape
The Global Hardware Encryption Market is characterized by intense competition among key players and hardware encryption solution providers offering a wide range of cryptographic hardware devices, embedded security solutions, and encryption technologies. Market players are focusing on strategic initiatives such as product differentiation, innovation, partnerships, and acquisitions to strengthen their market position and gain a competitive edge. Prominent players in the Hardware Encryption Market include:
· Kingston Technology Corporation
· Thales Group
· Samsung Electronics Co., Ltd.
· Western Digital Corporation
· Seagate Technology PLC
· Micron Technology, Inc.
· Toshiba Corporation
· Maxim Integrated Products, Inc.
· IBM Corporation
· Gemalto (Thales Digital Identity & Security)
These companies are actively involved in research and development, product commercialization, and market expansion initiatives to address evolving customer needs and emerging market opportunities.
|
Report Attribute/Metric |
Details |
|
Base Year |
2022 |
|
Forecast Period |
2023 – 2030 |
|
Historical Data |
2018 to 2022 |
|
Forecast Unit |
Value (US$ Mn) |
|
Key Report Deliverable |
Revenue Forecast, Growth Trends, Market Dynamics, Segmental Overview, Regional and Country-wise Analysis, Competition Landscape |
|
Segments Covered |
· By Algorithm (AES, RSA, ECC, Others) · By Architecture (ASIC, FPGA) · By Application (Consumer Electronics, Automotive, Healthcare, BFSI, Aerospace & Defense, Others) |
|
Geographies Covered |
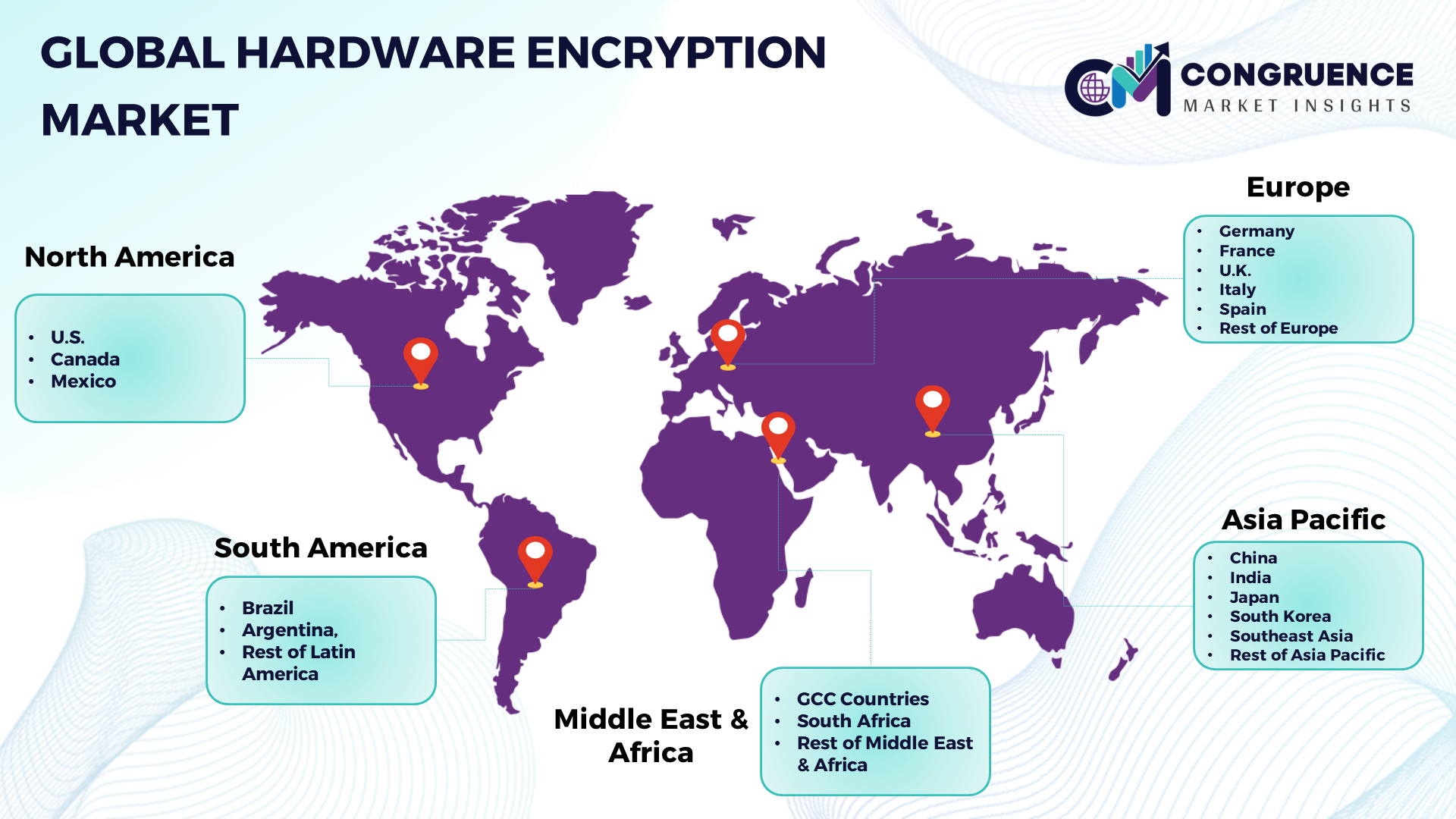
North America: U.S., Canada and Mexico Europe: Germany, France, U.K., Italy, Spain, and Rest of Europe Asia Pacific: China, India, Japan, South Korea, Southeast Asia, and Rest of Asia Pacific South America: Brazil, Argentina, and Rest of Latin America Middle East & Africa: GCC Countries, South Africa, and Rest of Middle East & Africa |
|
Key Players Analyzed |
Kingston Technology Corporation, Thales Group, Samsung Electronics Co., Ltd., Western Digital Corporation, Seagate Technology PLC, Micron Technology, Inc., Toshiba Corporation, Maxim Integrated Products, Inc., IBM Corporation, and Gemalto (Thales Digital Identity & Security) |
|
Customization & Pricing |
Available on Request (10% Customization is Free) |
